Import ACSC Windows Hardening Policies in Intune - Step by Step Instructions
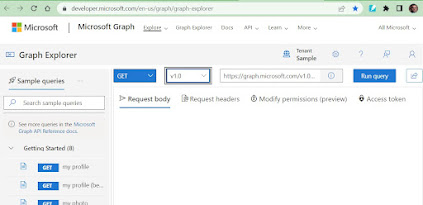
Step by Step instructions to create ACSC Windows 10 hardening settings in Intune using Graph API Microsoft have published Intune policies to comply with Australian Cyber Security Centre's (ACSC) Windows 10 Hardening Guidance . This policies are quite easy to import using graph explorer using official instruction provided at https://github.com/microsoft/Intune-ACSC-Windows-Hardening-Guidelines. However, this guide provides detailed steps by step instructions and screenshots to simply this process. To import these settings in Intune follow these steps 1. Navigate to Microsoft Graph Explorer . 2. Click on Sign in, login using authorised privileges in respective tenant i.e. Global Administrator 3. You may get a prompt to accept the consent, select Consent on behalf of your organization then click Accept. 4. Create a post request using Beta schema and type following query as shown in the screenshot, https://gr...